全部博文(106)
分类: 架构设计与优化
2014-04-02 04:54:40
We've talked about reverse proxy servers and how they can really be good at protecting the servers in your internal network. Lately, however, we've realized that some people actually think we're talking about forward proxy servers or that the two are one and the same. They're not. This post should easily spell out the differences between the two.
Just to make sure we're starting off on the same foot, the main purpose of a proxy service (which is the kind of service either of these two provide) is very similar to what a person aims to achieve when he proxies for another person. That is, to act on behalf of that other person. In our case, a proxy server acts on behalf of another machine - either a client or another server.
When people talk about a proxy server (often simply known as a "proxy"), more often than not they are referring to a forward proxy. Let me explain what this particular server does.
A forward proxy provides proxy services to a client or a group of clients. Oftentimes, these clients belong to a common internal network like the one shown below.
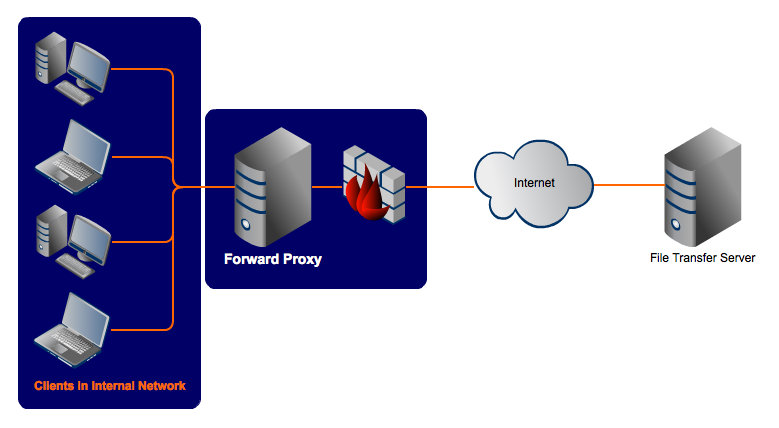
When one of these clients makes a connection attempt to that file transfer server on the Internet, its requests have to pass through the forward proxy first.
Depending on the forward proxy's settings, a request can be allowed or denied. If allowed, then the request is forwarded to the firewall and then to the file transfer server. From the point of view of the file transfer server, it is the proxy server that issued the request, not the client. So when the server responds, it addresses its response to the proxy.
But then when the forward proxy receives the response, it recognizes it as a response to the request that went through earlier. And so it in turn sends that response to the client that made the request.
Because proxy servers can keep track of requests, responses, their sources and their destinations, different clients can send out various requests to different servers through the forward proxy and the proxy will intermediate for all of them. Again, some requests will be allowed, while some will be denied.
As you can see, the proxy can serve as a single point of access and control, making it easier for you to enforce security policies. A forward proxy is typically used in tandem with a firewall to enhance an internal network's security by controlling traffic originating from clients in the internal network that are directed at hosts on the Internet. Thus, from a security standpoint, a forward proxy is primarily aimed at enforcing security on client computers in your internal network.
But then client computers aren't always the only ones you find in your internal network. Sometimes, you also have servers. And when those servers have to provide services to external clients (e.g. field staff who need to access files from your FTP server), a more appropriate solution would be a reverse proxy.
As its name implies, a reverse proxy does the exact opposite of what a forward proxy does. While a forward proxy proxies in behalf of clients (or requesting hosts), a reverse proxy proxies in behalf of servers. A reverse proxy accepts requests from external clients on behalf of servers stationed behind it just like what the figure below illustrates.
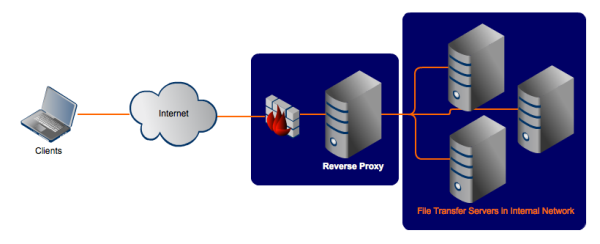
To the client in our example, it is the reverse proxy that is providing file transfer services. The client is oblivious to the file transfer servers behind the proxy, which are actually providing those services. In effect, whereas a forward proxy hides the identities of clients, a reverse proxy hides the identities of servers.
An Internet-based attacker would therefore find it considerably more difficult to acquire data found in those file transfer servers than if he wouldn't have had to deal with a reverse proxy. No wonder reverse proxy servers like are very suitable for complying with data-impacting regulations like PCI-DSS.
Just like forward proxy servers, reverse proxies also provide a single point of access and control. You typically set it up to work alongside one or two firewalls to control traffic and requests directed to your internal servers.
Both types of proxy servers relay requests and responses between source and destination machines. But in the case of reverse proxy servers, client requests that go through them normally originate from the Internet, while, in the case of forward proxies, client requests normally come from the internal network behind them.
In this post, we talked about the main differences between forward proxy servers and reverse proxy servers. If you want to protect clients in your internal network, put them behind a forward proxy. On the other hand, if your intention is to protect servers, put them behind a reverse proxy.
We recommend , a reverse proxy and load balancer that supports SFTP, FTP/S, HTTP/S, and other TCP-IP protocols. It comes with a fully-functional evaluation edition which you can download below.