黑马王子就是我! 技术认证:系统分析师,网络规划设计师,网络工程师,信息系统监理师,系统集成项目管理师,初级程序员,MCSE,MCDBA,CCNA 目前主攻虚拟化技术,VPN,系统架构,集群和高可用性等。
全部博文(516)
分类: 网络与安全
2016-06-07 15:44:40
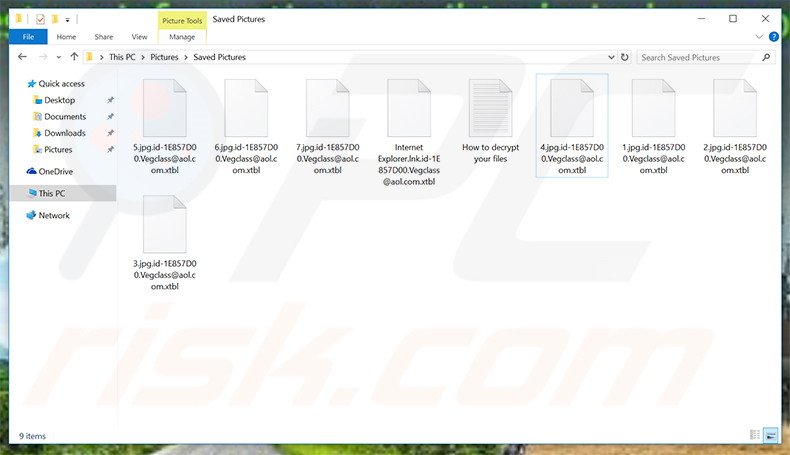
Vegclass is another ransomware infection identical to , , and . After stealthily infiltrating the system, Vegclass uses an asymmetric encryption algorithm to encrypt various files stored on victims' computers. During encryption, Vegclass ransomware adds the .Vegclass(@)aol.com.xtbl extension to the name of each encrypted file. It also changes the desktop wallpaper and creates a 'How to decrypt your files' text file, placing it in each folder containing encrypted files.
The text file and desktop wallpaper state that victims must contact developers of Vegclass to restore their encrypted files. As mentioned, Vegclass employs the asymmetric encryption algorithm and, thus, public (to encrypt) and private (to decrypt) keys are generated during encryption. The private key is unfortunately stored on Command and Control (C&C) servers controlled by cyber criminals (developers of Vegclass). Therefore, to restore files, victims must purchase the private key for a certain fee (which is currently unknown). To receive payment instructions, victims must send three selected files to the email address provided. Bear in mind, however, that developers of ransomware-type viruses often ignore victims regardless of any payments made. Therefore, we strongly advise you not to contact cyber criminals or pay any ransom. In doing so, you will simply support their malicious businesses. Unfortunately, there are currently no tools capable of decrypting files compromised by Vegclass. Therefore, victims can only restore their files/system from a backup.
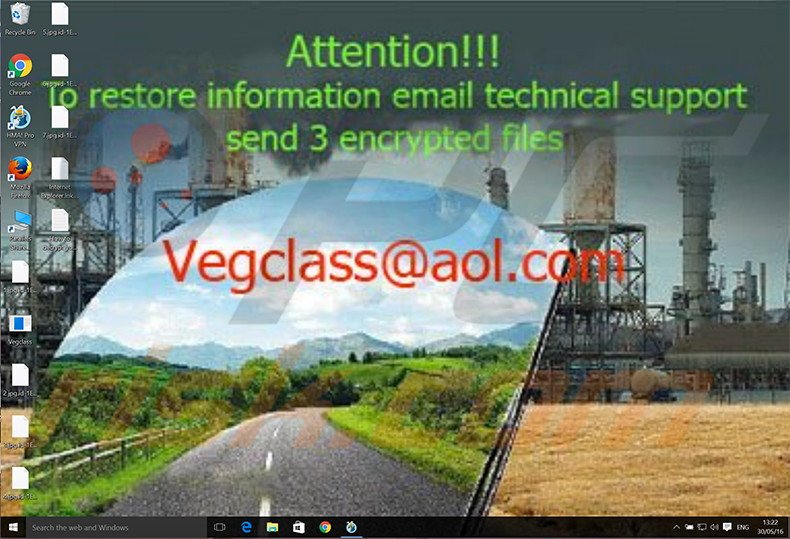
Screenshot of a message encouraging users to contact the developers of Vegclass ransomware to decrypt their compromised data:
All ransomware-type viruses are very similar - they encrypt victims' files and demand ransom payments. There are two main differences - the type of encryption algorithm used and size of ransom. Research shows that these viruses are mostly distributed using malicious email attachments, P2P (peer-to-peer) networks, fake software updates, and trojans. Therefore, never download files from third party sources or open attachments sent from unrecognized/suspicious email addresses. In addition, keep your installed software up-to-date and use a legitimate anti-virus/anti-spyware suite. The existence of ransomware-type malware is one of the main reasons why you should maintain regular backups of your files.
Text presented in Vegclass desktop wallpaper:
Attention!!! To restore information email technical support send 3 encrypted files Econvector3(@)aol.com or Eco_vector(@)india.com
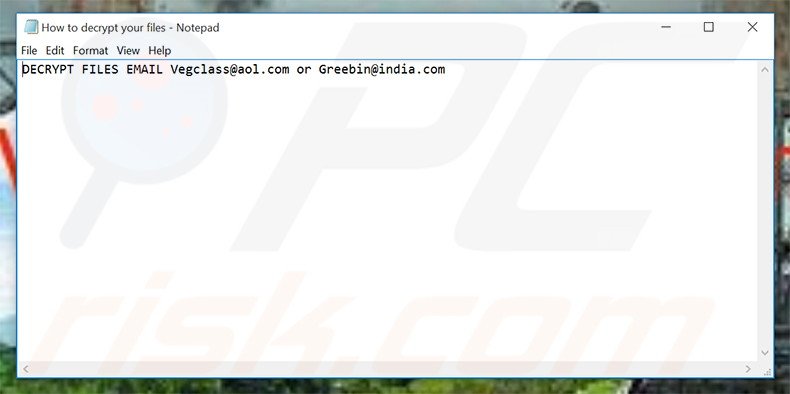
Screenshot of Vegclass ransomware text file (How to decrypt your files.txt):
Text presented within this file:
DECRYPT FILES EMAIL ecovector3(@)aol.com or eco_vector(@)india.com
Screenshot of files encrypted by Vegclass:
Quick menu: