Social websites like Facebook or Twitter tend to be the number one channel to distribute new malware in 2011. This time a new bot targets Twitter users and spreads via the microblogging service. Emsisoft Anti-Malware detects this malware as Worm.Win32.Ngrbot. Read this article to learn more about this new outbreak and how to protect against it.
The malicious files we received show the picture of a woman as icon with a file name being in the format ”facebook-pic% number%.exe”, which in our analysis shows that the malware is quite dangerous.
When executed, Ngrbot extracts the main file of his body to the directory “C:\Documents and Settings\%username%\Application Data\” on test machines running Windows XP. The used filename is generated using the HDD serial number as the initial key. If the malware however fails to get the HDD serial number, it will then use “1337B00B” (read: elite languages) as initial key.
One of its “features” is to block the access to various security sites, including emsisoft.com. So indirectly it prevents security programs from performing updates. The body of the worm contains the blocked sites names within the encrypted section .data:
In addition, Ngrbot also downloads a text file that is located at hxxp://212.7.214.16/list.txt, which contains 1269 sites domain and blogs related to computer security. This means it is also able to update the list of pages that are blocked.
As a self-defense, this malware also has rootkit capabilities to hide its presence on the created files and registry entries. Ngrbot performs a system wide hook to inject itself into the whole process and hooks some of the following APIs:
- advapi32.dll.RegCreateKeyExW
- advapi32.dll.RegCreateKeyExA
- ntdll.dl.NtQueryDirectoryFile
- ntdll.dl.NtEnumerateValueKey
- ntdll.dl.NtResumeThread
- ntdll.dl.LdrLoadDll
- kernel32.dll.CopyFileW
- kernel32.dll.CopyFileA
- kernel32.dll.CreateFileW
- kernel32.dll.CreateFileA
- kernel32.dll.MoveFileW
- kernel32.dll.MoveFileA
- wininet.dll.InternetWriteFile
- wininet.dll.HttpSendRequestW
- wininet.dll.HttpSendRequestA
- ws2_32.dll.getaddrinfo
- ws2_32.dll.send
- nspr4.dll.PR_Write
And, Ngrbot marks its presence in the infected system with a mutex named “s5rBKCUVfOF8JLVi” and “hex-Mutex”.
On the API list you can see several functions associated with the network/Internet, meaning that Ngrbot can monitor browsing activities of its victim. This malware communicates with the host or C&C server through the IRC protocol, so it can transmit any information found on the victims computer to the author. Additionally the author is able to instruct the malware to do something, like for example download another malicious file or to update the malware binary file.
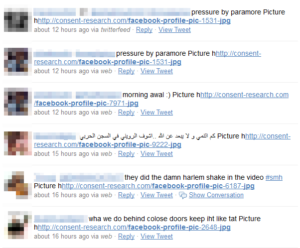
This is obviously very dangerous – if the victim logs into his email, Facebook, Twitter, or even online banking account these are not safe any more. One example is shown in the picture above, the string was found in a hijacked process:
Here you can see some online banking sites like officebanking.cl, Alertpay, Moneybookers and PayPal.
On the infected computer Ngrbot collects several pieces of information like the IP address and country of origin by connecting to
On our test machine, the default page of the browser was also modified, leading to the site hxxp://redirecturls.info/ which then redirects to the following sites:
- hxxp://best-articles.li
- hxxp://bestarticles-ever.blogspot.com
- hxxp://amazingarticles.info
- hxxp://mega-articles.info
The MSN Messenger is also used as one of the spreading tools. What the bot does is to intercept messages sent by the user and then hijack the message on-the-fly.
For example in this case I try to send the message “Hello” to a friend, but apparently my friends actually get the message “LOL http://[MALICIOUS_LINK]“. The malicious URL being received can vary, depending on what is instructed by the host server. Furthermore the malware will report this action to the host server.
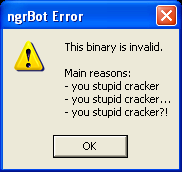
However, the author of Ngrbot seems to have a sense of humor despite being a criminal – he leaves some messages to those trying to crack and analyze his malware.