分享工作和学习中的点点滴滴,包括前端、后端、运维、产品等各个方面,欢迎您来关注订阅!
分类: LINUX
2021-04-25 17:49:02
| 最流行的两种SSH身份验证机制是基于密码的身份验证和基于公钥的身份验证。使用SSH密钥通常比传统的密码身份验证更安全和方便。 |
客户端:8 192.168.43.137
服务端:CentOS8 192.168.43.139
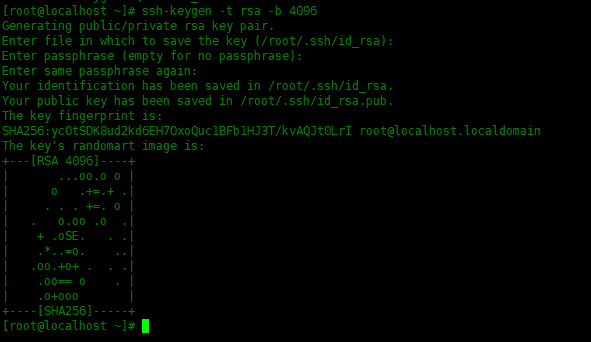
通过输入以下,生成新的4096位的SSH密钥对:
[root@localhost ~]# ssh-keygen -t rsa -b 4096 Generating public/private rsa key pair. Enter file in which to save the key (/root/.ssh/id_rsa): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /root/.ssh/id_rsa. Your public key has been saved in /root/.ssh/id_rsa.pub. The key fingerprint is: SHA256:ycOtSDK8ud2kd6EH7OxoQuc1BFb1HJ3T/kvAQJt0LrI root@localhost.localdomain The key's randomart image is: +---[RSA 4096]----+ | ...oo.o o | | o .+=.+ .| | . . . +=. o | | . o.oo .o .| | + .oSE. . .| | .*..=o. ..| | .oo.+o+ . . .| | .oo== o . | | .o+ooo | +----[SHA256]-----+
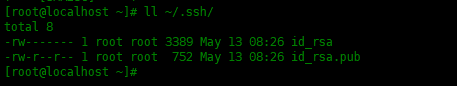
想要验证是否生成了新的SSH密钥对,使用ls -l查看~/.ssh目录是否有刚才生成的文件:
[root@localhost ~]# ll ~/.ssh/ total 8 -rw------- 1 root root 3389 May 13 08:26 id_rsa -rw-r--r-- 1 root root 752 May 13 08:26 id_rsa.pub
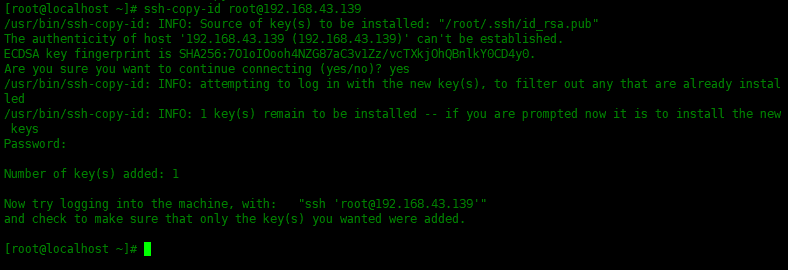
将公钥复制到远程服务器,使用ssh-copy-id实用程序,输入远程服务器的root密码:
[root@localhost ~]# ssh-copy-id root@192.168.43.139 /usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/root/.ssh/id_rsa.pub" The authenticity of host '192.168.43.139 (192.168.43.139)' can't be established. ECDSA key fingerprint is SHA256:7O1oIOooh4NZG87aC3v1Zz/vcTXkjOhQBnlkY0CD4y0. Are you sure you want to continue connecting (yes/no)? yes /usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed /usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys Password: Number of key(s) added: 1 Now try logging into the machine, with: "ssh 'root@192.168.43.139'" and check to make sure that only the key(s) you wanted were added.
也可以使用以下命令复制公钥:
[root@localhost .ssh]# cat ~/.ssh/id_rsa.pub | ssh root@192.168.43.139 "mkdir -p ~/.ssh && chmod 700 ~/.ssh && cat >> ~/.ssh/authorized_keys && chmod 600 ~/.ssh/authorized_keys"
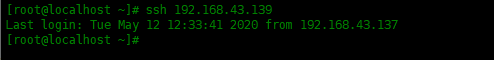
使用以下命令登录ssh服务器:
[root@localhost ~]# ssh 192.168.43.139 Last login: Tue May 12 12:33:41 2020 from 192.168.43.137
登录服务器端,关闭密码认证:
[root@localhost ~]# ssh 192.168.43.139 Last login: Tue May 12 12:33:41 2020 from 192.168.43.137 [root@localhost ~]# vim /etc/ssh/sshd_config 搜索一下三条,将选项改为No PasswordAuthentication no ChallengeResponseAuthentication no UsePAM no
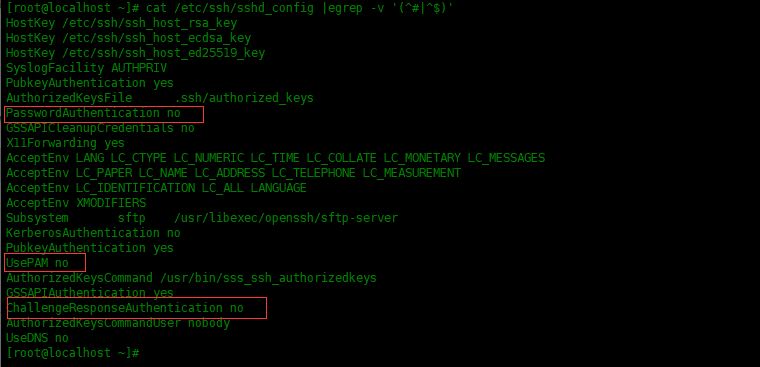
重启sshd服务:
[root@localhost ~]# systemctl restart sshd
可以使用同一密钥管理多个远程服务器。默认情况下,SSH的端口是TCP 22。更改默认SSH端口可降低自动攻击的风险。